@tmntwitw said:
I have not seen the dump file, but assuming that the passwords are hashed and salted, I think it won't be a trivial task for someone to derive the original password from the hash? (Not a security expert here, so I might be wrong)
But yeah, one should still change the password.
From what I’ve seen they’ll have the code from configuration.php which is all that is needed to at least turn service passwords into plain text. So it’s not just billing passwords you need to change.
Also email history in WHMCS may contain passwords generated for new services in plain text. For hosts who never changed it in email templates (not sure if WHMCS changed it themselves later), email history at least used to contain plain text passwords written by the user on registration.
User on OGF that is going through the DB dump says they had ID's and other KYC verification in the dump, as well. So, that's makes this even worse for some.
New email they allegedly sent out just now(from OGF)
Immediate Action Required: Security Breach and Data Leak Update
We are contacting you to address a critical security incident that has impacted our systems and potentially your data.
Incident Timeline and Immediate Actions:
December 16th, 2023 - Initial Breach Detected: Our team discovered unauthorized access in our WHMCS system and promptly notified all users.
Proactive Security Measures: We initiated a fresh installation on a new server for enhanced security and to mitigate further risks.
Data Leak Confirmation:
December 28th, 2023 - Data Compromise Identified: Despite our actions, we have ascertained that certain data from the initial breach has been exposed online.
Detailed Overview of the Leaked Data:
Client Information: Names, addresses, phone numbers, and email addresses.
Financial Data: Billing addresses, payment histories, and partial credit card details.
Service and Purchase Records: Details of hosting plans, ASN registrations, and other services.
Support and Communication Logs: Information from support tickets and email communications.
Login Credentials and Security Data: Usernames, hashed passwords, security questions, and API keys.
Custom Fields and Administrative Data: Additional client-specific information and administrative user data.
Audit Logs and System Settings: Records of user actions and configurations within the system.
Impact Beyond Cloudie Networks:
Wider Industry Effect: The breach has repercussions for several providers, especially those using modules like WHMCSServices and WHMCSGlobalServices.
Lack of Complete Provider List: Unfortunately, a comprehensive list of all affected providers is not available.
Our Commitment to Enhanced Security:
Selective Module Usage: To safeguard your information, we have discontinued the use of all third-party modules, with the exception of the Lagom theme.
Infrastructure Security: We have migrated to a new server with upgraded security protocols to fortify our defenses against such incidents.
Urgent Recommendations for Your Safety:
Immediate Password Reset: Change your Cloudie Networks password using [Password Reset Link] and consider updating passwords on other platforms if they are similar.
Account Monitoring: Stay vigilant for unusual activities in your accounts and report any anomalies.
Beware of Phishing: Cloudie Networks will never ask for sensitive information via email. Use [Official Contact Link] for any verification.
Additional Safety Measures Taken:
Payment Information Security: We have cancelled all PayPal subscriptions and revoked/reissued Stripe card API tokens to prevent unauthorized charges.
Resetting of Compromised Credentials: We've reset all leaked VM and Proxmox credentials as a preventive action.
Staying Updated and Supported:
Ongoing Updates: We will keep you informed about any new developments.
Support Availability: We is ready to assist at Cloudie.sh Support. But please be aware that delays may occur due to the level of large volume of requests at the current time.
Our Assurance:
We are deeply committed to the security of your data and are taking all necessary steps to prevent such incidents in the future. We sincerely apologize for any inconvenience caused and appreciate your cooperation during this critical time.
Best Regards,
Cloudie Networks, LLC.
@MannDude said: OGF says Cloudie's Discord mods are deleting mentions who bring it up in their chat, and nothing has been sent to their customers from Cloudie yet.
Can confirm they do some crazy damage control, I was banned before I even managed to join, for some reason.
WHMCSServices was mentioned previously, since it appeared to be a supply chain attack where they were hacked, and the hackers then sent an email with a file link to 'update' a module used which was what allowed access to other user's WHMCS. Is that correct?
This is the first I'm hearing of WHMCSGlobalServices being in the mix of blame, can anyone confirm?
I would hope that was just a one time deal and he is not handing out the link to everyone who asks.
I do, everyone who reached out was a long time member that was most likely affected and wanted to check for himself. Everyone with malicious intents already have it, its public, I'm not doing anyone any harm by providing it to affected people.
@treesmokah are you still giving the download link to people
Yes.
I do, everyone who reached out was a long time member that was most likely affected and wanted to check for himself. Everyone with malicious intents already have it, its public, I'm not doing anyone any harm by providing it to affected people.
I would hope that was just a one time deal and he is not handing out the link to everyone who asks.
I do, everyone who reached out was a long time member that was most likely affected and wanted to check for himself.
I would consider passing around links to a hacked data base of customer information a black hat activity.
I would like to hear other members thoughts on this.
I would hope that was just a one time deal and he is not handing out the link to everyone who asks.
I do, everyone who reached out was a long time member that was most likely affected and wanted to check for himself.
I would consider passing around links to a hacked data base of customer information a black hat activity.
I would like to hear other members thoughts on this.
I can stop If you want, but I find gatekeeping already public leak to be pointless. Nobody with malicious intents will come here and request it from me.
I personally do not find anything what I did wrong, I did due diligence on people requesting it and decided to pass it to them.
Cloudie presented misleading information stating no personal information was leaked, so I'd rather want affected people to not take his words on the leak and check for themselves.
It can also be used for research and documenting his incompetence and negligence.
In my mind it is not that the information is known to be out in the wild, it's a question of if passing that data around is the right thing to do for a white hat forum. In my mind you should stop as people already know if they are affected because the hackers have probably already notified them directly.
It's out in the wild, with more leaks being dumped of other providers. Don't see an issue with treesmokah, they haven't posted any links publicly or looking to gain from it. Sad for anyone that's been breached... quite awful
I would hope that was just a one time deal and he is not handing out the link to everyone who asks.
I do, everyone who reached out was a long time member that was most likely affected and wanted to check for himself.
I would consider passing around links to a hacked data base of customer information a black hat activity.
I would like to hear other members thoughts on this.
I can stop If you want, but I find gatekeeping already public leak to be pointless. Nobody with malicious intents will come here and request it from me.
I personally do not find anything what I did wrong, I did due diligence on people requesting it and decided to pass it to them.
Cloudie presented misleading information stating no personal information was leaked, so I'd rather want affected people to not take his words on the leak and check for themselves.
It can also be used for research and documenting his incompetence and negligence.
I would prefer if you stopped doing it, at least on LES.
the DB is stolen from Cloudie and handing out stolen property/goods is a felony in my book.
If people are interested in the DB for ”research” or to ”check ” if their data is in it.
Since its in the public, let them search for it.
And they should already know if they are, or have been, a customer. In that case they should assume that their data has been sold/given away to other people and change their password (if they haven’t already).
I’m not saying that I’m an expert in GDPR, but spreading other peoples personal information (as you do by gicing out links to the DB), even you could face charges in the EU.
In general I don't see a problem with passing around the link because it's widely available. However, I doubt this forum is the right place for it and thus it shouldn't be distributed here. Making aware that there's a public link is ok but we shouldn't be a place where things like this are exchanged, it's a different scope.
Comments
User on OGF that is going through the DB dump says they had ID's and other KYC verification in the dump, as well. So, that's makes this even worse for some.
[ IncogNET LLC ] - Since 2020
[ The Internet Speech & Privacy Company ]
And this was suspected and 99% confirmed by a lot of people already last week.
New email they allegedly sent out just now(from OGF)
I received this email, so can confirm that it is more than alleged to have been sent.
Although I didn't compare the quoted version word-for-word
Can confirm they do some crazy damage control, I was banned before I even managed to join, for some reason.
Email suggests that the original breach may have occurred from module(s) provided by https://www.whmcsservices.com/ or https://whmcsglobalservices.com/ ?
WHMCSServices was mentioned previously, since it appeared to be a supply chain attack where they were hacked, and the hackers then sent an email with a file link to 'update' a module used which was what allowed access to other user's WHMCS. Is that correct?
This is the first I'm hearing of WHMCSGlobalServices being in the mix of blame, can anyone confirm?
[ IncogNET LLC ] - Since 2020
[ The Internet Speech & Privacy Company ]
@treesmokah are you still giving the download link to people
youtube.com/watch?v=k1BneeJTDcU
I would hope that was just a one time deal and he is not handing out the link to everyone who asks.
Yes.
I do, everyone who reached out was a long time member that was most likely affected and wanted to check for himself. Everyone with malicious intents already have it, its public, I'm not doing anyone any harm by providing it to affected people.
I just sent a dm. Thnx
I would consider passing around links to a hacked data base of customer information a black hat activity.
I would like to hear other members thoughts on this.
I can stop If you want, but I find gatekeeping already public leak to be pointless. Nobody with malicious intents will come here and request it from me.
I personally do not find anything what I did wrong, I did due diligence on people requesting it and decided to pass it to them.
Cloudie presented misleading information stating no personal information was leaked, so I'd rather want affected people to not take his words on the leak and check for themselves.
It can also be used for research and documenting his incompetence and negligence.
In my mind it is not that the information is known to be out in the wild, it's a question of if passing that data around is the right thing to do for a white hat forum. In my mind you should stop as people already know if they are affected because the hackers have probably already notified them directly.
It's out in the wild, with more leaks being dumped of other providers. Don't see an issue with treesmokah, they haven't posted any links publicly or looking to gain from it. Sad for anyone that's been breached... quite awful
I would prefer if you stopped doing it, at least on LES.
the DB is stolen from Cloudie and handing out stolen property/goods is a felony in my book.
If people are interested in the DB for ”research” or to ”check ” if their data is in it.
Since its in the public, let them search for it.
And they should already know if they are, or have been, a customer. In that case they should assume that their data has been sold/given away to other people and change their password (if they haven’t already).
I’m not saying that I’m an expert in GDPR, but spreading other peoples personal information (as you do by gicing out links to the DB), even you could face charges in the EU.
In short, let interested people search for it.
“Technology is best when it brings people together.” – Matt Mullenweg
In general I don't see a problem with passing around the link because it's widely available. However, I doubt this forum is the right place for it and thus it shouldn't be distributed here. Making aware that there's a public link is ok but we shouldn't be a place where things like this are exchanged, it's a different scope.
All right, I will.
Thanks for presenting your points, I'm sure I wouldn't be prosecuted for it, but I respect you.
To clarify, we can still discuss the breach but do not spread the material.
“Technology is best when it brings people together.” – Matt Mullenweg
Yeah - name who else got hacked and why the fuck I did spam on my phonenumber (-:
Haven't bought a single service in VirMach Great Ryzen 2022 - 2023 Flash Sale.
https://lowendspirit.com/uploads/editor/gi/ippw0lcmqowk.png
thai provider: https://secure.jvh.co.th/
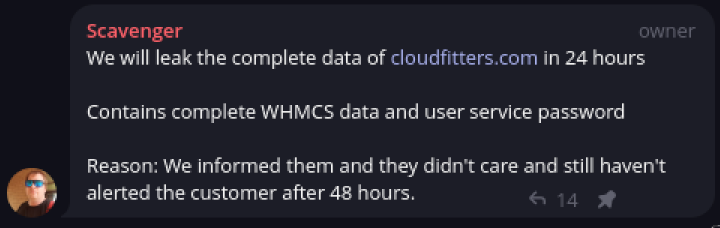
https://cloudfitters.com
Another one https://managedway.com/
https://bgp.tools/as/53292
They seem fairly large.
oh they're big, rip
Oof.
What's the word on the cause of these? Third party WHMCS module? Something else? I've seen some conflicting info.
[ IncogNET LLC ] - Since 2020
[ The Internet Speech & Privacy Company ]
Everything points to WHMCSServices, attacker 100% has access to their DB and probably pushed infected versions of addons.
More info on ManagedWay
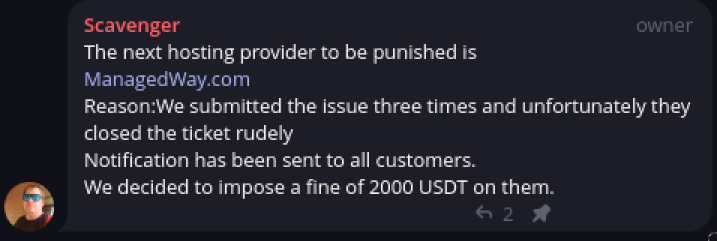
That's what I thought as well, but I thought there was some screenshots shared here or on the OGF that indicated that may not be the case. 🤷♂️
[ IncogNET LLC ] - Since 2020
[ The Internet Speech & Privacy Company ]
Attackers sent out emails using their systems.

Its "supposed" to be leaked soon.
whmcssec just joined LES
Free NAT KVM | Free NAT LXC
More providers hit, https://hostersale.com/, https://serverwala.com/(name I recognize for some reason) and https://the23.digital/. I have not verified the data.
Maybe @whmcssec is willing to discuss specifics?